Multi-factor Authentication is
critical in today's world. Many Organizations already adopted this model
from a long time and today's blog post is written to provide you with some
essential resources with a Quick demo to experience the benefits of Azure MFA.
What is Azure Multi-Factor
Authentication?
Multi-factor authentication (MFA)
is a method of authentication that requires the use of more than one verification
method and adds a critical second layer of security to user sign-ins and
transactions. It works by requiring any two or more of the following
verification methods:
- Something you know (typically a password)
- Something you have (a trusted device that is
not easily duplicated, like a phone)
- Something
you are (biometrics)
Multi-factor authentication
is a method of verifying who you are that requires the use of more than just a
username and password. It provides a second layer of security to user sign-ins
and transactions.
Azure Multi-Factor Authentication
helps safeguard access to data and applications while meeting user demand for a
simple sign-in process. It delivers strong authentication via a range of easy
verification options—phone call, text message, or mobile app notification or
verification code and 3rd party OATH tokens.
How it works ?
Read the complete information
available in each section on this above article
Methods available for
multi-factor authentication
- phone call
- text message
- mobile app notification—allowing users to
choose the method they prefer
- mobile app verification code
- 3rd party OATH tokens
Available versions of Azure Multi-Factor Authentication
- Multi-Factor Authentication for Office 365
- Multi-Factor Authentication for Azure
Administrators
- Azure Multi-Factor Authentication
Check what is available with each version before you adopt the MFA using
- Feature comparison of versions Section
How to get Azure Multi-Factor Authentication
- Purchase Azure Multi-Factor Authentication licenses and assign them to your users.
- Purchase licenses that have Azure Multi-Factor Authentication bundled within them such as Azure Active Directory Premium, Enterprise Mobility Suite or Enterprise Cloud Suite and assign them to your users.
- Create an Azure Multi-Factor Authentication Provider within an Azure subscription.
Billing options
- Per user or Per Authentication model
Be sure to read to know the Pricing
Most important part to review is to adopt the best one for your needs
Choose the multi-factor security solution for you : On premises or cloud
These are the basics to begin
your learning.
Microsoft has provided great
documentation articles as one of the essential resources when you begin your
learning with Azure MFA.
For Office 365 below is the
essential one
Currently we have
about 40 documentation available on the Azure MFA topic and you can access them
below
Some vital articles
to read for a successful MFA deployment
- Directory integration between Azure MFA Server
and Active Directory
- Getting started with Azure Multi-Factor
Authentication and Active Directory Federation Services
- Getting started with the Azure Multi-Factor Authentication Server
- Securing cloud resources with Azure
Multi-Factor Authentication and AD FS
- Secure cloud and on-premises resources using
Azure Multi-Factor Authentication Server with AD FS 2.0
- Secure cloud and on-premises resources using
Azure Multi-Factor Authentication Server with Windows Server 2012 R2 AD FS
- Azure Multi-Factor Authentication FAQ
Update:
Review the new Security Best practices article for Azure MFA
More Organizations
already use ADFS to secure their environment and now with MFA it adds more one
more layer of strong authentication to provide a highly secure access to end
users without compromising the Organization's Information Security.
Once you are done
with the documentations, you can view some demos with deep dive discussion
from Microsoft Virtual Academy course intended on this topic
Its now time for a
Quick demo walk-through with my own experience.
I have setup MFA in
the cloud and chose Azure Multi-factor authentication for my Office 365 users.
*You can Setup MFA from Office 365 Portal for free and additionally you don't need create a Authentication provider as shown below, I am planning to use some advanced features so, explicitly selected Azure MFA in Cloud for demo.
Also Azure MFA comes as a part of your Azure AD premium and EMS. For this demo I am using the MFA Authentication provider .
Here is the Azure
portal view showing my Multi-Factor Authentication Provider
I have selected a
test account and configured the Authentication contact info with my Mobile
number
Already my test
account is enforced for MFA and below is the snapshot
If I navigate to the
Service Settings, I have options to configure App passwords, Skip multi-factor
authentication for federated users in the intranet and also Suspend MFA for
remembered devices.
Since I have already
configured the Azure Multi-Factor Authentication as Authentication provider, I
can take advantages of the advanced features.
I can Navigate to the
MFA portal by accessing the Go to the Portal Hyperlink
For Instance I am
showing an example of Usage Reports, I can generate the report for a set of
time frame for analysis.
More options are
available and the above one is an example.
Lets get in to the
end user experience, My user is trying to access his Office 365 Webmail and
below is the experience he gets before successfully authenticates to his inbox.
If you take a look at
the steps Pic 4 Indicates the user is authenticating for the
call he received and after successful authentication he will be accessing his
inbox, which is shown in Pic 9.
I voluntarily
failed the authentication to show you the another method, using Text
message with the Verification code.
In Pic 5 the
authentication is failed and user is provided with alternative options in Pic
6 I am selecting the Text Me option and successfully receiving the
code in the next pics and finally accessing my Inbox.
This is a pretty regular
experience with Azure MFA, we can do more than this and hope this one is good with
a quick demo.
Note: Selecting Alternative authentication method when primary authentication method failed shown above is available by default in Azure MFA. The same experience was not available in On premises Azure MFA Server, until the recent MFA server version 7.0.0 released with this feature inclusion.
Update:
Review the below excellent office blog post showcasing end user experience with MFA
Sign in to Office 365 with a second verification method
Up Next, We have
the Office 2013 device apps now support multi-factor authentication
through the use of the Active Directory Authenticaton Library (ADAL).
Currently this is in preview and you can test this by enabling Modern
authentication for your tenant.
Before I conclude, I
want to share you with one more great TechNet blog post, I came across recently
that is pretty new and shows us how to use MFA Support for Windows
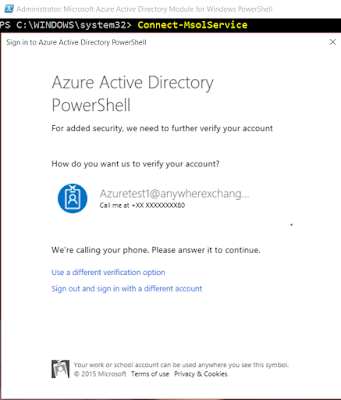
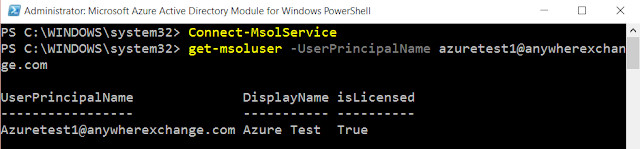
Azure Active Directory PowerShell Module.
Hope this write-up is
quite useful for readers to know Azure MFA a bit better with the curation of
various resources under a single window with bits of my own experience and
learning.